The vaccines widely used by humans today -- especially those used to protect children against mumps, measles, and other potentially deadly ailments -- are what we'd call "perfect" vaccines. But new research suggests that "imperfect" or "leaky" vaccines -- ones that don't make their hosts totally immune to the disease and incapable of spreading it to others -- might have a surprising downside. For now, this so-called leakiness only exists in vaccines used to treat farm animals. But researchers warn that as humankind tackles bigger, badder diseases, we should keep the potential danger of leaky vaccines in mind.
In a study published Monday in PLOS Biology, researchers led by Andrew Read, the Evan Pugh Professor of Biology and Entomology and Eberly Professor in Biotechnology at Penn State University and Venugopal Nair, the Head of the Avian Viral Diseases program at The Pirbright Institute studied Marek's disease -- a herpes virus that infects chickens.
[Anti-vax mom changes her tune as all 7 of her children come down with whooping cough]
Highly contagious, Marek's disease didn't used to be deadly. But now chicken farmers see increasingly virulent strains in their broods. The vaccine keeps chickens from getting sick, but unvaccinated chickens are getting sicker than they used to.
Read and his colleagues don't know whether the vaccines for the disease actually caused more virulent strains of the illness to develop. It's not a clean-cut evolutionary partnership the likes of antibiotics and antibiotic resistant bacteria.
But according to their research, however those more dangerous strains have developed, it's the existence of the vaccine that allows them to continue existing.
[New class of antibiotic found in dirt could prove resistant to resistance]
Imagine for a moment a chicken with Marek's disease so viral (otherwise known as a particularly "hot" strain of the virus) that it knocks them dead within 10 days. Marek's used to be a disease that didn't kill, but lingered. It took a while to transmit from one chicken to another. Ten days simply wasn't enough time, so the hot strain would die with one or two unfortunate chickens.
Now imagine that this super-hot chicken has been vaccinated, and that this vaccine saves its life -- but doesn't keep it from spreading its supercharged Marek's. Suddenly that lucky little chicken is patient zero.
"We had laid out the mathematics in a previous paper, and suggested this might be happening," Read told The Post. To prove it, they found themselves some unvaccinated birds and put them in close quarters with infected-but-protected birds to watch the disease spread.
"The experiment shows that strains too hot to exist in an unvaccinated world can actually persist when there's a leaky vaccination," Read said.
This isn't such a big deal for the chicken industry at the moment, Read explained, since it's trivial to make sure all of your birds are vaccinated when they live on a farm. And Marek's only affects chickens.
[There’s really bad news for egg lovers]
"The problems would start if we weren't just talking about chickens," he said. If a leaky avian flu vaccine was given to chickens, for example, those chickens would still be capable of spreading hot strains to wild fowl -- like ducks and geese -- who couldn't be so easily vaccinated.
And the problem gets scarier when you ask what happens if a human gets a particularly hot strain of avian flu.
"It's just not possible to predict if a virus will get more or less nasty when it jumps species," Read said. "It's not predictable in general, and we just don't know how that works with avian flu. It's just not a good idea to create these conditions."
Read and his colleagues stress that their findings have nothing to do with the human vaccines that some parents demonize. Immunologists outside the study were quick to affirm this.
"It’s important not to interpret this study as an argument against vaccination of our children against flu or any other disease," Peter Openshaw, president of the British Society for Immunology and Professor of Experimental Medicine at Imperial College London (who wasn't involved in the study) told the Science Media Centre. "The standard vaccines that are in current use are safe and effective, and not prone to cause the emergence of more dangerous strains of viruses. Vaccines are amongst the safest and most cost-effective measures that we have to improve public health and protect from disease and it is vital that we achieve high vaccination rates to prevent the return of the many and terrible diseases that they prevent," he said.
[Vaccine deniers stick together. And now they’re ruining things for everyone.]
The authors of the new study heartily agree, but they do hope that those developing the next generation of vaccines -- ones to treat diseases like HIV and Malaria -- will proceed with caution.
Because it's basically impossible to build up a natural immunity to these diseases, it's likely that the first successful vaccines will be imperfect -- and perhaps even leaky the way the Marek's vaccine is in chickens.
But the study authors -- as well as other scientists -- stress that a leaky vaccine is better than none for many human illnesses. Because HIV, Ebola, and malaria are devastating killers, even an imperfect vaccine would be a medical breakthrough.
[FDA approves new Roche Ebola test for emergency use]
"In the future, [the findings] could apply to vaccines that we hope will be developed against generally lethal viruses (e.g. HIV, Ebola), encouraging scientists to strive towards “perfect vaccines” for them," Michael Skinner, a virologist from Imperial College London who wasn't part of the study, told the Science Media Centre. "However, these viruses are very different from [Marek's]. Without intervention, both of these are generally lethal already. Ebola, as we have so tragically seen recently, can also be effectively transmitted even after death."
So while this effect could well be seen in human diseases one day, it would probably only happen in viruses so devastating that vaccines are still the best hope. Scientists will just have to be sure they understand how the vaccine's implementation might effect the spread of the virus.
[EU regulator recommends 1st license for malaria vaccine]
"To me, it doesn't mean that we shouldn't use imperfect vaccines," Read said. "Let's say we become certain that a Malarial vaccine is going to drive the evolution of more dangerous Malarial parasites. That just means we have to be aware of how to avoid transmission."
The answer is higher vaccination rates wherever possible, Read explained -- not the abandonment of vaccines. And simple measures -- like mosquito nets -- could prevent the unvaccinated from exposure to any super-hot strains that resulted from the lifesaving injection.
http://www.washingtonpost.com/news/speaking-of-science/wp/2015/07/27/leaky-vaccines-could-make-viruses-more-deadly-new-study-suggests/
950 million Android phones can be hijacked by malicious text messages
Booby-trapped MMS messages and websites exploit flaw in heart of Android.
Zimperium
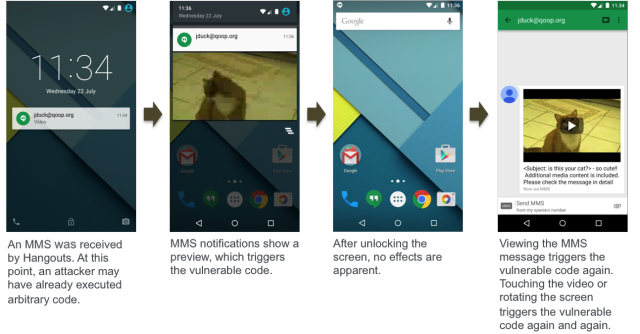
Almost all Android mobile devices available today are susceptible to hacks that can execute malicious code when they are sent a malformed text message or the user is lured to a malicious website, a security researcher reported Monday.
The vulnerability affects about 950 million Android phones and tablets, according to Joshua Drake, vice president of platform research and exploitation at security firm Zimperium. It resides in "Stagefright," an Android code library that processes several widely used media formats. The most serious exploit scenario is the use of a specially modified text message using the multimedia message (MMS) format. All an attacker needs is the phone number of the vulnerable Android phone. From there, the malicious message will surreptitiously execute malicious code on the vulnerable device with no action required by the end user and no indication that anything is amiss.
In a blog post published Monday, Zimperium researchers wrote:
A fully weaponized successful attack could even delete the message before you see it. You will only see the notification. These vulnerabilities are extremely dangerous because they do not require that the victim take any action to be exploited. Unlike spear-phishing, where the victim needs to open a PDF file or a link sent by the attacker, this vulnerability can be triggered while you sleep. Before you wake up, the attacker will remove any signs of the device being compromised and you will continue your day as usual—with a trojaned phone.The vulnerability can be exploited using other attack techniques, including luring targets to malicious websites. Drake will outline six or so additional techniques at next month's Black Hat security conference in Las Vegas, where he's scheduled to deliver a talk titled Stagefright: Scary Code in the Heart of Android.
Drake said all versions of Android after and including 2.2 are potentially vulnerable and that it's up to each device manufacturer to patch the bug. So far, very few devices have been patched, leading him to estimate that about 95 percent of devices—or about 950 million of them—are currently susceptible. Even Google's Nexus 5 handsets, which typically receive security fixes long before most other Android handsets—remain vulnerable. Nexus 6 devices, meanwhile, were patched only recently against some but not all Stagefright attacks. Vulnerable devices running Android versions prior to 4.3 (Jelly Bean) are at the greatest risk, since earlier Android versions lack some of the more recent exploit mitigations. Fixes require an over-the-air update.
Enter Firefox
Interestingly, the Stagefright vulnerability also affects Firefox on all platforms except Linux, and that includes the Firefox OS. Firefox developers have patched the vulnerability in versions 38 and up."If you install Firefox 38, you can no longer get exploited directly via Firefox," Drake told Ars. "However, if I make your Firefox download the malicious video instead of trying to play it with a
SilentCircle, maker of the Blackphone Android handset, has also patched the vulnerability in its PrivatOS with the release of version 1.1.7.
Android is designed with a security sandbox that prevents most apps from being able to access data used by other apps. That goes a long way to containing the damage Stagefright and similar code-execution exploits can do. In theory, for instance, it should prevent Stagefright exploits from sniffing login credentials used by a properly designed banking app. Still, Drake warned that successful exploits at the very least provide direct access to a phone's audio and camera feeds and to the external storage. Worse still, many older phones grant elevated system privileges to Stagefright code, a design that could allow attackers access to many more device resources.
"The attacker would have remote arbitrary code execution and thus escaping the sandbox is only a small step away," Drake said. He said existing root exploits, including those known PingPongRoot, Towelroot, and put_user, would likely help an attacker break free of the sandbox and gain much wider control over a vulnerable device.
For now, there's not much end users can do to protect themselves other than to install a patch as soon as one becomes available for their specific Android device. People can also prevent MMS messages from automatically loading in Google Hangouts or other text apps. That will prevent malicious code from being automatically loaded but won't protect against other attack vectors. There's no indication that the bug is being actively exploited in the wild. Google has thanked Drake for privately reporting the vulnerability and has since made a patch available to partners. But as we all know, it can take years for security fixes to reach some models, and many devices never receive them.
http://arstechnica.com/security/2015/07/950-million-android-phones-can-be-hijacked-by-malicious-text-messages/
No comments:
Post a Comment